THE DEVELOPMENT OF DISPLAYING SSL CERTIFICATES IN A BROWSER
Displaying an SSL certificate in a browser is one of the aspects of using the internet. This originally unremarkable problem has gradually become a big topic, which affects not only security, but marketing as well. Let us look at how displaying SSL certificates in browsers has developed. You might be surprised how often this changes and how much it has deviated from its original purpose.
Encrypting the web with an SSL certificate has its origins in the 1990s. One of the first certification authorities – Thawte – was founded in 1995 and is still very popular today. The HTTP and HTTPS web protocols for encrypted web have been with us (with forced modernization) for 20 years.
Connecting to the internet was not common for computer users at the time, and web encrypting was an exception.Besides, until 2007, there were only two types of certificates – simple ones without information about the owner (domain validated, DV), and certificates with verified information about the owner (organization validated, OV).
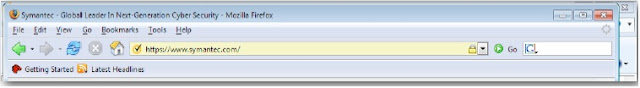
As a result, the lock icon appeared in the status bar (typically in Internet Explorer 7 and 8 browsers). The situation started changing with new competition, and browsers started informing users about HTTPS more. In its first version (2004), Firefox used a lock icon similar to Explorer, but later it highlighted certificates in blue.
In its very first version (2009), Chrome dealt with displaying certificates in a similar way. However, as it already knew EV certificates, it was able to write the details of the organization.
In 2007, CAB forum (certification authority browser forum) released a new certificate type with extended verification.Its main contribution was to display the name of the organization next to the address bar. This item is called “EV green bar“ - and it really was green in the past.
In the older versions of Internet Explorer, the whole web address bar with an EV certificate had a green background.This very noticeable feature was, unfortunately, used only in Microsoft browsers. Nowadays, the browsers do not display a whole line with coloured background, but only a small part with the name of the organization next to the address bar. This was probably the ideal version of displaying an EV certificate.
Recently, there has been a trend of “decoloring” the green bar, which was started by Mozilla. Their “green bar” has been getting gradually lighter over the years, and now it is more white than green, with very subtle green text. For a user, this is certainly less beneficial than in the past. Chrome has adopted this colouring and the originally green address bar looks almost identical in both browsers.
After the introduction of the first iPhone 2007, smartphones and later tablets grew in popularity. Most internet users nowadays access the internet from a mobile device rather than a desktop.
In mobile browser versions, a typical black lock usually symbolizes SSL certificates on a website. An EV certificate is not displayed as a green bar but as the name of the organization in green font.
These days, mobile devices can deal with certificates without problems, the same as desktops. However, displaying the certificate detail is more complicated because it is done by tapping the lock icon, which requires dexterity.
A true revolution – but not in a positive sense of the word – was caused by Microsoft's browser EDGE. In 2015, it issued a successor for Internet Explorer, which shocked, besides other things, by the fact that it does not enable display of an SSL certificate's detail on a website. Therefore, you cannot view its detail, and its authentication aspect with the data verified by a certification authority is compromised. You can see the name of the organization in a green bar only in the case of EV certificates with extended verification.
At the end of 2016, Google published the results of a study, which was looking for ideal security symbols for security warnings in a browser. Because of this study, three new symbols were created in order to simplify the browser notifications. The survey established that for these symbols, the icon is significant, not the colour. It turned out that browser users do not mind whether the warning is red, blue or black; the colour is not directly related to the character of the message and the majority does not understand red as a warning. Therefore, Chrome focuses mainly on a clear symbol and it displays one of three symbols for different statuses – a green lock, an informative “i” and a red triangle.
Firefox is planning to adopt the results of the study, but for now, it uses its own symbols. An average certificate is displayed with a green lock, and an EV certificate has the name of the organization in green letters on a light bar.
These days, we have been witnessing the greatest simplification of browsers. Microsoft's Edge did not worry about certificates and simplified them. Now it is not possible to find information about a certificate. Apparently, Google got inspired and probably also believes that certificate details are not useful for the user. After clicking on the green bar or on the lock icon, the certificate details do not show, you have to use the F12 button to see them.
Mozilla does display the certificate detail, albeit after several clicks. However, if there is a security problem (e.g. if you receive an untrustworthy certificate), there are problems with displaying it. The certificate is displayed in Base64, which is too complicated for most users.
Securing websites is a hot topic now and it certainly receives the most attention. Almost every internet user is,nowadays, aware how important it is to protect their personal and confidential information. After 10 years with EV certificates, the market has reached the point when they are not only used by banks and financial institutions, and website owners consider it a benefit to their visitors when the certificates' importance, from the authentication point of view, is respected.
Therefore, it is surprising that browser producers have decided to remove certificate details, despite the fact that they have tried to teach users for years to check their own security. One possible explanation might be the future development of HTTP/2 and the fact that all domains will be secured by a certificate in the future. Nevertheless, even then it will be desirable to check certificate information and origins on the website.
I hope that the occurring problems will be noticed by browser producers and that they will go back to the conservative design. If that is not the case, we will have to verify the certificate details on a website with OpenSSL, which is not very user friendly.
Displaying an SSL certificate in a browser is one of the aspects of using the internet. This originally unremarkable problem has gradually become a big topic, which affects not only security, but marketing as well. Let us look at how displaying SSL certificates in browsers has developed. You might be surprised how often this changes and how much it has deviated from its original purpose.
ThE BEGINNINGS
Connecting to the internet was not common for computer users at the time, and web encrypting was an exception.Besides, until 2007, there were only two types of certificates – simple ones without information about the owner (domain validated, DV), and certificates with verified information about the owner (organization validated, OV).
As a result, the lock icon appeared in the status bar (typically in Internet Explorer 7 and 8 browsers). The situation started changing with new competition, and browsers started informing users about HTTPS more. In its first version (2004), Firefox used a lock icon similar to Explorer, but later it highlighted certificates in blue.
In its very first version (2009), Chrome dealt with displaying certificates in a similar way. However, as it already knew EV certificates, it was able to write the details of the organization.
THE ARRIVAL OF EV CERTIFICATES
In the older versions of Internet Explorer, the whole web address bar with an EV certificate had a green background.This very noticeable feature was, unfortunately, used only in Microsoft browsers. Nowadays, the browsers do not display a whole line with coloured background, but only a small part with the name of the organization next to the address bar. This was probably the ideal version of displaying an EV certificate.
Recently, there has been a trend of “decoloring” the green bar, which was started by Mozilla. Their “green bar” has been getting gradually lighter over the years, and now it is more white than green, with very subtle green text. For a user, this is certainly less beneficial than in the past. Chrome has adopted this colouring and the originally green address bar looks almost identical in both browsers.
The Development of Mobile Devices
In mobile browser versions, a typical black lock usually symbolizes SSL certificates on a website. An EV certificate is not displayed as a green bar but as the name of the organization in green font.
These days, mobile devices can deal with certificates without problems, the same as desktops. However, displaying the certificate detail is more complicated because it is done by tapping the lock icon, which requires dexterity.
Revolution of Microsoft with Edge
Simplifying Security Indicators
Firefox is planning to adopt the results of the study, but for now, it uses its own symbols. An average certificate is displayed with a green lock, and an EV certificate has the name of the organization in green letters on a light bar.
Hiding the Certification Detail Due to Simplification
Mozilla does display the certificate detail, albeit after several clicks. However, if there is a security problem (e.g. if you receive an untrustworthy certificate), there are problems with displaying it. The certificate is displayed in Base64, which is too complicated for most users.
What next?
Therefore, it is surprising that browser producers have decided to remove certificate details, despite the fact that they have tried to teach users for years to check their own security. One possible explanation might be the future development of HTTP/2 and the fact that all domains will be secured by a certificate in the future. Nevertheless, even then it will be desirable to check certificate information and origins on the website.
I hope that the occurring problems will be noticed by browser producers and that they will go back to the conservative design. If that is not the case, we will have to verify the certificate details on a website with OpenSSL, which is not very user friendly.