Firmware emulation
Let’s understand the meaning of emulation in simple words. Suppose you get a firmware file (bin/img) from any source, like their official website, and you want to run the firmware file, i.e. img/bin file. How can you run it? There are two ways:
1. Hardware Emulation – In this, you get a hardware device, like a router, and you upload the firmware file onto the router and interact with the firmware via an interface. The issue with this method is you always need a hardware device to run the firmware.
2. Software Emulation – In this, we use software instead of hardware. The software mounts the firmware and you interact with the firmware. The biggest advantage using this method is you don’t need any hardware and you can run as much as firmware you wish to.
Let’s start Firmware Emulation using the software emulation method.
Tools
We can make use of the following tools for Software Emulation
1. QEMU– QEMU is the emulator used for emulating firmware. More info on QEMU can be obtained here – QEMU-INFO. For setting up QEMU please refer to – QEMU-SETUP and for firmware emulation demo – QEMU-DEMO
2. Firmware Analysis Toolkit (FAT) – FAT is the toolkit used for firmware emulation. It uses tools such as Firmadyne, Binwalk, Firmware Mod Kit, MITM Proxy and Firmwalker for emulation. Please refer to FAT for setting up FAT on your system. We will use this tool for exploiting blind command injection.
Please download Netgear Firmware for the demo.
Step by step procedure for firmware Emulation along with the screenshots:
Step 1 – Copy Netgear Firmware in Firmadyne folder as shown:
Step 2 – Run fat.py script and enter following information as highlighted:
After pressing enter, it will ask you for your password two or three times. Enter the same password you have used for setting up firmadyne. In my case, the password is firmadyne, and after entering the password, wait for two minutes and it will give you the IP address of the firmware as shown below:
Step 3 Accessing via Browser – Enter the IP address obtained in step 2. It may happen that you may not be able to access the firmware in your 1st attempt. Try it four or five times and you will surely get access to the firmware login page.
Step 4 Login with username/password – admin/password and you should be logged in as shown:
Exploiting command Injection
Here are the steps we will follow:
1. Extract the firmware for viewing the source code of the file present in the firmware.
2. Inspect source code for Blind Command Injection exploitation.
3. Request the file via Browser.
4. Intercept the HTTP request of the file via Proxy Tool (Burp Suite, Paros, etc.) and change the parameters.
5. Exploit Blind Command Injection.
Let’s start.
Extract the firmware using binwalk -e option (I have presented the whole process on my blog post called Reversing Firmware for Extracting Hard-Coded Telnet Credentials) and follow the steps as highlighted in the screenshot:
We are in the _rootfs.squashfs.extracted folder which contains all the files present in the firmware. Now we need to find php files present in the firmware and it can be done using the command find . -name “*.php”
Command Explanation
find – name of the command
. – starting from current directory
*.php – any file ending with .php extension
This command will list all the php files present in the firmware as shown:
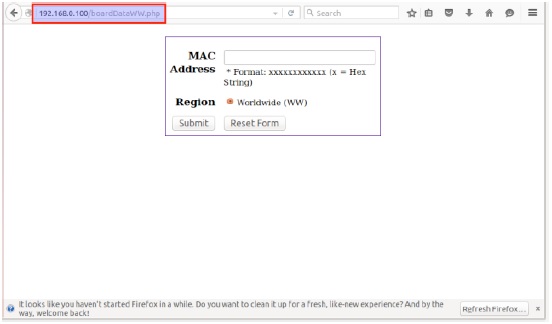
A file exists called boardDataWW.php that asks for MAC Address as shown below. File boardDataWW.php is present in home/www/ folder.
Let’s see the source code of the boardDataWW.php file.
As highlighted, parameter macAddress is passed to exec command (2nd highlighted part) and the input is not filtered (1st highlighted). exec is the function in php used for executing OS commands. The input is taken as is, thus we can pass OS commands as well with the macAddress parameter.
Intercept all the request responses in the Firefox browser. You can use Burp Suite, Paros, OWASP ZAP, etc. I am using Burp Suite and the process for intercepting in Firefox can be found here – Burp-For-Firefox.
Intercept the Firefox request as shown:
Send this request to repeater tab by right clicking on it and selecting repeater option. Now we can enter any command in the macAddress field and check the response. Let’s enter 001122334455 -c ; ls # in the macAddress field.
Command Explanation:
; – Terminate the first input.
# – Whatever comes after # will be treated as comment.
So we are asking exec function to execute mac_address_value -c ; our_command.
As seen, the response is Update Success! We were expecting a list of directories in the response since we have passed ls command but we received Update Success in response. What does it mean? It means our command was executed successfully but it did not return the result of our command, i.e list of directories on browser. This is a typical example of Blind Command Injection.
Let’s exploit Blind Command Injection by outputting the result of ls command in a file as shown:
Now let’s access demo.txt from browser and see the output:
It returns a list of all the files present in the firmware. Similarly, we can execute any OS command and get the output in demo.txt file.