Well Known Vendors in Networking
Information available on Security Focus
Tutorial 1 – Core Principles
Welcome to the “Attacking Network Devices” workshop. In this workshop
you will gain diversified knowledge, covering network and security threats
in networks that will build your knowledge about network security issues
and how you can practice different methods of attacking networking nodes
to enhance your skills.
This workshop is designed in a way to cover all levels of students, from
beginners level to intermediate professionals. Moreover, if you are a
newbie in the network industry, by completing this workshop, you will add
enough knowledge to boost your career in the network security field.
However, if you want to gear up and experience network security then
you should first build your knowledge about the top vendors and their
products that play a core role in the networking industry. Once you have
that then you can move towards gaining experience with the selected
product or vendor and gain further hands-on knowledge in order to step
up in the industry.
This workshop will cover top networking and network security vendors and
top products that a security professional should have experience with. But
this is not easy. Its not like playing with Linux or Windows Operating
Systems. Such network devices use different operating systems, which
are a bit difficult to get legally, and network courses are expensive that
offer an opportunity to gain hands-on experience.
Here, in this workshop, you will get a chance to learn how you can setup
your virtual home lab and run such network devices in a virtual
environment so that you gain hands-on experience and not just the
bookish knowledge, plus you can practice as much as you want as you
build your own virtual networking lab.
This sounds awesome for an individual who doesn’t have any experience
and wants to jump into this field but at the same time, if you are already
working in networking industry and want to move to network security
field, don’t worry this workshop will cover this, too.
Let’s begin our journey of this workshop and first have a quick look at the
industry footprint to find who is doing what and what will be best for you
to take up as a career.
Top Players in Internetworking
Internetworking is a broad industry and you cannot simply put a tag on
anyone in particular that this is a top player in the networking industry as a Vendor. There is segregation from a product specific standpoint and the
product features at most.
When we talk specifically about the internetworking industry, there are
three to four key products or devices that basically form the core of the
entire Internet world, hence internetworking too. Features and modules of
such devices differentiate the services these devices can perform for any
corporation, however, the core concepts don’t change regarding those
specific devices.
This workshop will cover the basics of such devices that present the core
functionalities of these devices and not specific version or features.
These devices include:
Now, first we’ll cover the core functionalities for each of these devices so
that you have the correct concept for each of them.
Routers
In its simplest definition, it is a device to connect two different networks
and performs routing in between them. This is their core functionality, to
route packets from one network to another.
Switches
In its simplest definition, it is a device to connect multiple hosts or
systems or network nodes within a same network to switch packets on
layer two of OSI Model.
Intrusion Detection System / Intrusion Prevention System
It is a network device that you would require to detect abnormal network
traffic as per your network requirements, that’s the detection part. These
abnormal packets are considered intrusions in a generic form. Prevention
is basically blocking those packets from entering your network, which is
basically blocking the intrusion attempts.
Firewalls
This device basically filters network packets and provides network access
level control to network devices that can talk to other nodes in the
network. They come in a variety of types based on their functionality.
However, the main function is filtering packets but their usage extends to
more advance technologies, like VPN
Now, let’s further study which vendor provides such devices and is
considered the top provider in the same technology.
Cisco Systems – The Giant
Cisco is a giant in networking products. In the market front they look like
a hardware company but in actual it’s a software company that produces
internetworking operating systems. Cisco is considered a market leader in
routing & switching as a major contributor but not as a vendor who
provides devices like firewalls and IDS/IPS. However, Cisco also has a
good chunk of the firewall / ID / IPS market as well.
In short, Cisco is everywhere in the networking business, ranging from
small business to service provider networks.
Juniper networks
Unlikely Cisco System, Juniper Networks are well known in their security
products rather than routers and switches. There is no comparison of
Juniper with Cisco Systems if you talk about Routers & Switches.
Checkpoint Software Technologies
Considered the industry leader in security products ranging from firewalls
to intrusion prevention systems. Well known in threat prevention and
security management.
However, the major chunk of interworking devices are routers and
switches as they form the backbone of the Internet and security devices
are there to protect the data packet flow and security the Internet.
So what did you learn? If you want to attack the network devices, you
should be good enough in handling routers and switches, and get handson experience with these devices at a minimum so that you are
comfortable playing with these devices. However, it’s expensive to buy
such devices or get training all the time. Don’t worry, on this workshop
platform you will learn how to setup a home lab and get your hands dirty
in attacking network devices.
You learned that the Internet is based on routing and switching performed
by routers and switches, and these are basically hardware devices running
a cutting edge operating system to perform these tasks for you. So
gaining hands-on experience requires a thorough understanding and
experience of operating systems run by these network devices.
On Cisco routers & switches, and in fact all of their products, the
operating system that is used is Cisco priority and it is called IOS
(originally internetwork operating system). This workshop will make you
practice this operating system in your own home virtual lab which will be
covered in an upcoming module.
As these devices form the core of Internet, the operating systems of these
devices have faced many threats and many vulnerabilities exist which
were discovered by security researchers. We have presented a metric
below so that you can have an idea how hackers have been taking control
of these devices by exploiting the discovered vulnerabilities.
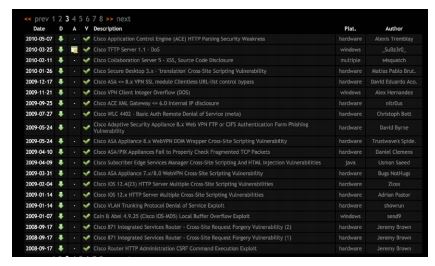
Vulnerabilities Lookup from Famous Exploit – DB.com
Information collected is available on exploit-db website which you can see
yourself, we have just presented the quick search for vulnerabilities on
Cisco products
On the security focus website you can search a range of security
vulnerabilities so far discovered in Cisco products by selecting the
following options, here only one vulnerability info is presented for proof of
concept.
Cisco Security Advisories
Cisco itself publishes Security Advisories for significant security issues that directly involve Cisco products and require an upgrade, fix, or other customer action but do not provide vulnerability details that could enable someone to craft an exploit. All security advisories on Cisco.com are displayed in chronological order, with the most recently updated advisories as shown below. You can browse and go through these advisories on below link.
Cisco advisory link: http://tools.cisco.com/security/center/publicationListing.x
For a security professional, it is important to track the latest vulnerabilities
and, if possible, get hands-on experience. To achieve this goal, you will
learn how to setup your own virtual lab at home in the next module. So
far, the workshop has been informative and thank you for attending this
workshop and join us in the next module to get some hands-on
experience too.