Evading Firewalls and Intrusion Detection Systems
Tutorial 1 - Understanding Firewalls and IDS
Welcome to the fourth & last module of this workshop. We hope you have been attending the complete previous three modules and have earned good knowledge so far in this workshop. Let’s now move towards the Firewall and Intrusion Detection Systems. In order to attack such devices, an attacker should have a thorough understanding and experience with
these devices.
You should understands how they work and what are the different types and which of these devices are most commonly available in the industry. The workshop flow wowill uld take you through the concepts of evading these devices and how little tools can help you find information behind firewalls. This module will be based more on concepts rather than just hitting tools and knowing nothing in background.
What is Firewall?
A firewall is hardware or software, or it can be a combination of both, designed in such a way which will prevent unauthorized access or activities. This can be bidirectional for dedicated hosts or networks. The best place to install a firewall in the network is at the gateway or between two networks or placed before your network where it is connecting to a public network, like the Internet.
Firewall Architecture
There are three main and common types of firewall architecture that can be used based on the requirements. There are known as:
● Bastion Host
● Screened Subnet
● Multi-home Firewall
Bastion Host
System designed to protect network resources from unauthorized access and it basically has two network interfaces that connect to different networks, like public and private.
Screened Subnet
It is also called DMZ or subnet and it basically has servers that provide different services to public networks, like the Internet. Its main job is to prevent unauthorized access to DMZ Network as well as Private network.
Multi-homed Firewall
It has more than three interfaces which allows further subdivision of the network based on the security requirements of the corporate network.
The above architecture of firewalls are basically based on how you designed your network and your security need. There are different types of firewalls that are placed or used in the above three architectures as per the corporate network security requirements.
The types basically identify how the firewall is operating in order to protect your corporate network. So there are two key things you should remember at this stage. Firstly where you should place the firewall and secondly what type of firewall is required in your corporate network
Types of Firewalls
In the network security industry there are basically four main types of firewalls, which are mostly deployed in the corporate networks, as listed below.
● Packet Filtering Firewall
● Circuit Level Firewall
● Application Level Firewall
● Stateful Multilayer Inspection Firewalls
Packet Filtering Firewall
This type of firewall works at the network level of the OSI Model and is commonly found as part of the routers. Such firewalls compare packets against the set criteria before it leaves the firewall. Based on the criteria, packets can be dropped or forwarded to the next hop devices.
Circuit Level Firewall
They work on the session layer of the OSI Model, and monitor the TCP handshaking to find out whether sessions are legitimate or not, however, they don’t filter each individual packet but keep the local network anonymous.
Application Level Firewall
They are named “Application Level firewalls” because they work on the Application layer of the OSI Model. They protect applications like Web Applications, FTP Servers, telnet or any other applications.
Stateful Multilayer Inspection Firewalls
These types of firewalls are a combination of all three types of firewallsand provide deep packet inspection and protection.
How to Evade Firewalls?
Well, this is not an easy topic to understand until you have a strong grip on TCP/IP and have hands-on experience with any command line type firewall like “iptables” than you can easily play with the evasion techniques in order to evade firewalls. However, there is no set principle
by virtue of which you can say that if you use that technique you going to evade a firewall easily.
No, that doesn’t work any more, it all depends on how well you understand the targeted network and how good you are in the firewall technology deployed at the target corporate network.
Use common sense man!
But, there are still ways to evade the firewalls. Consider that you have to perform penetration testing for a web application, that is running behind a firewall, and blocks access based on packet filtering! So what? Yes, the firewall has to open ports 80 or 443 which are used by http/https, respectively, and that’s all you want to have access to.
Now, in such scenarios, it’s really easy to do and it’s by simply using a small bit of logic. Don’t run extensive scans by using tools like “nmap”, “Nessus” or by any other means, because you don’t need to, as your actual target is web application and not the underlying operating system, so it’s useless to run scans and alert the network administrator to block your IP Address.
Tutorial 2 – Fire-walking
Firewalking is a trick that hackers have used extensively for long time and you may still find it working for you at times when you will face less experience administrators configuring the firewall.
Firewalking is basically a technique that is used to perform information gathering about systems that are behind a firewall. Different tools performthis but your Swiss army knife “the nmap” can also do this for you.
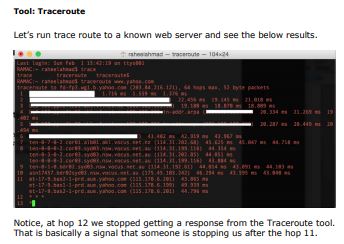
However, there is even a very basic tool that can help you detect the
systems behind the firewalls.
And you can see that we found the host running on hop 12 with the IP
address shown. Now you can run “nmap” scans on the discovered IP
Address, however, we will not do it here live as it’s “yahoo” server and not
our own virtual lab. But we will present the techniques you can use to
scan the targets behind the firewall.
Fragmented Packets Scans
Nmap has the ability to fragment the packets while scanning with the -f
option so it can bypass the packet inspection performed by the firewalls.
The syntax of nmap scan is:
# nmap –f target.ip.address
Source port number specification
Administrators most of the time allow all incoming traffic that comes from
a specific port number. nmap can use this misconfiguration error to help
you perform firewalking and ports that can be easily used are 53, 80, 20
or any other port which you have to gather information for. Syntax is
given below and you can try this on below server as well.
# nmap --source-port 53 scanme.nmap.org
Random Order Scan
In such scan basically you can scan the number of hosts in random order
rather than sequential scan. This scan type basically is combined with
slow timing options in the nmap command. It is very effective if you don’t
want to alert administrators by generating more logs.
# nmap --randomize-hosts 192.168.1.10-15
If you want to thoroughly understand nmap, it is recommended that you
read the nmap manual mage. You can find direct information of evading
firewalls and IDS with nmap at http://nmap.org/book/man-bypassfirewalls-ids.html
Let’s move towards Intrusion Detection Systems and discuss if they can
be evaded too.
Intrusion Detection Systems
In their simple definition they are the systems that detect abnormal
behavior in the network that we call intrusions. A simple “IDS” is
sometimes also referred to as “packet-sniffer”, and this “packet-sniffer”
sniffs the packets and later these packets are analyzed to detect
intrusions based on the set rules or principles.
Methods of Detecting Intrusion in the Network
● Signature Based
● Anomaly Based
● Protocol Anomaly Detection
Types of Intrusion Detection Systems
Based on their scope and the nature of detecting intrusions, they are
categorized into four categories:
● Network Based Intrusion Detection System
● Host Based Intrusion Detection System
● Log File Monitoring
● File Integrity Checks
Is it possible to evade Intrusion Detection Systems?
Answer: Yes
However, you need to be familiar with the methods of detection on which
these systems work.
Signature based Evasion (Obfuscation)
Since signature based Intrusion Detection Systems work on the available
signatures in their repository, if you design an attack vector which is not
available in the repository as a attack type than you can easily bypass the
“IDS”. Another method could be slightly changing the attack method so
you can easily bypass the “IDS”. Firewalking techniques also work to an
extent in order to bypass “IDS”
Encryption
SSL VPNs are designed to allow portable, easy to setup, encrypted
sessions between client stations and the corporate network which can be
used in performing attacks as well.
IDS DOS Attack
Another technique which is sometimes useful in bypassing the IDS is to
shutdown the IDS first by denial of service attack. Once it’s down, no one is there in the network to detect you but it is extremely rare and difficult
to do so.
Techniques for evading intrusion detection systems depend on the skill set
of the attacker. To present the demonstration, we would require a
network lab setup, and this will be covered in the upcoming workshop