Basics of Hacking
Hacking is famous and is among the most searched words on search engines. It’s always been an interesting topic for school students. Hacking is an extra mile from the normal information technology field. You need to know many things if you want to peruse your career in the field of ethical hacking or security testing.
Prerequisites
• Knowledge of TCP/IP protocols
• Basic knowledge of Metasploit framework
• Prior hands-on experience with Virtual Machines
• Understand general concepts of networking technologies
• Experienced in any one operating system [Linux, Windows & OSX]
• Understands the basics of hacking terminologies, e.g. exploit, payload, vulnerability
• Prior experience with any network based security scanners
• Basic knowledge of Metasploit framework
• Prior hands-on experience with Virtual Machines
• Understand general concepts of networking technologies
• Experienced in any one operating system [Linux, Windows & OSX]
• Understands the basics of hacking terminologies, e.g. exploit, payload, vulnerability
• Prior experience with any network based security scanners
What we will cover
As we have just mentioned, learning hacking requires you to know many things, however, we will present for you in a nutshell how to perform ethical hacking but our workshop is limited to focusing on key steps involved in ethical hacking.
Basic Concepts
Hacker, the one who breaks, or tries to break, the security measures illegally in order to gain an access or authorization, not limited to what he or she doesn’t have for any system, application or networks.
The industry, trying to be clever, has categorized such types of individuals in three different types as per their motives.
The Types: generally, information security industry has categorized three types of hackers as defined below.
Black Hats These are the experts in computer security with a wide range of extraordinary computer hacking and cracking skills, however, their motive is always destructive or malicious. They are also named as crackers and always offensive in nature.
Gray Hats These are the security experts with a wide range of information security experience and computer hacking skills, however, their motive in not always destructive. They work both offensive and defensive at various times. They are best fit in between white hats and black hats.
Sometimes they find bugs & vulnerabilities in various applications and systems and at the same time directly report to the vendor for improving security.
White Hats They are information security professionals who have earned experience skills and have industry recognitions by means of affiliation with different vendors. They are information security people hired by different organizations. They are certified ethical hackers. White hats are always defensive in nature.
Hacktivism is defined as anything in hacking that has a political agenda. It can be performed by any kind of hackers except white hats. An individual who performed such act is termed as hacktivist.
Confidentiality is satisfaction or assurance that the information that is supposed to be accessed by only a set of individuals is actually only accessible to those people.
Integrity is something which is accurate and unchanged and it’s the trustworthiness of the data or resources.
Availability is the assurance that the systems, applications or resources and data are actually available as required.
Vulnerability is generally defined as the weakness; it could be in the design, source of the application, and configuration in the information technology environment including people – processes – technologies.
Threat is a combination of vulnerability and the motivation factors. Threat is sometimes also defined as any circumstances or event that can lead to a disastrous situation.
Exploit is a malicious piece of software code that is written to gain illegitimate access to the information technology environment. Exploits are written to gain the motive by making use of weaknesses in the respective environment. It is simply designed as a way to breach the information security controls.
Payload is simply a part of an exploit; payload is the actual piece of code, which is written to perform specific tasks.
Zero-Day is an attack in which a hacker exploits the certain vulnerability before the launch of any patch from the vendor for this vulnerability.
Ethical hacking & Penetration Testing
Ethical hacking and penetration testing don’t have anything different in them and they are just two different terminologies presenting the same theory.
Penetration testing gathers the information about the actual attack footprint of your organization’s overall security, depending on the scope of the work.
In this workshop, we will talk about the 90/10 principle that we will cover in upcoming modules in more granular details.
A one line summary is “penetration testing is actual exploitation of vulnerabilities by means of ethical hacking”.
Virtual Lab Setup
We will be delivering a step-by-step guide to build your own lab so that you can practice the workshop at your desk. Lab requirements:
• Virtual Box Software
• Ubuntu Linux
• Nmap
• Nessus Home Feed
• NeXpose
• Metasploit Framework
• Vulnerable Operating System (Metasploitable)
Step 1 – Installing Virtual Box Software
Download Link: https://www.virtualbox.org/wiki/Downloads.
Select & download the binary, as per your operating system requirement. In my case, I will be installing the VirtualBox-4.3.12-93733-OSX from the above download link as shown below.
Next, double click the icon as shown in step 1 in above figure.
Next, continue to install by clicking the continue button.
Next, begin installation by clicking the continue button
Next, select the installation location or customize the installation as shown above, however, it is recommended to leave the settings as default and hit installation.
Next, successful installation will show the below screen.
Virtual box installation is now complete.
Step 2 – Installing Ubuntu Linux
We have successfully completed the installation of Virtual Box software. Now let’s install the Ubuntu Linux operating system to build the lab on top of Ubuntu Linux as Operating System. First we need to get the latest copy of the Ubuntu Linux Operating System. Based on your hardware architecture, you can select the ISO to download.
Download Link for Ubuntu Linux: http://www.ubuntu.com/download/desktop.
For your ease of access we have provided the above link for the downloading of Ubuntu Linux operating system and below is the snapshot of the said link.
We have successfully downloaded the copy of the Ubuntu Linux Operating System.
Next is setting up of Virtual Machine to run this Ubuntu Linux operating system. Let’s begin, starting the Virtual Box and follow the following sequential steps to setup a new virtual machine and install the Ubuntu Linux.
Next is creating a new virtual machine. In this step, we will name the virtual machine and set the type as Linux and the version as Ubuntu Linux (64-bit).
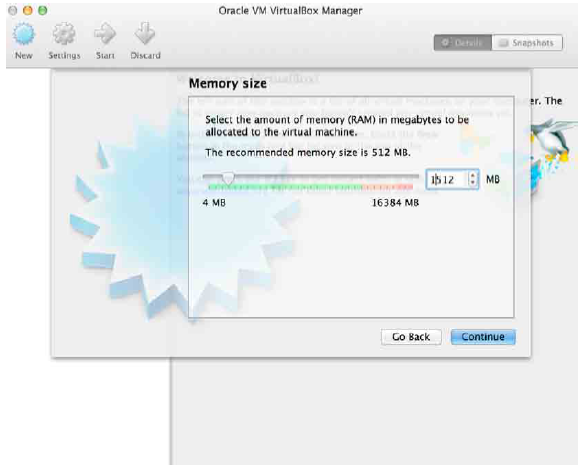
Next, click continue and follow the next step as shown below to configure the memory size for your new virtual machine. It is recommended to set the memory size as 1512 MB.
Next, click continue and follow the next step as shown below to configure your new virtual machine’s hard drive.
Next, click create and follow the next step to configure the hard drive file type. It is recommended to use VID as the file type for the hard drive.
Next, click the continue button and follow the next step to configure the storage on physical drive and it is recommended to dynamically allocate the memory.
Next, click continue and follow the next steps to allocate the hard drive file and size. It is recommended to keep the size as 26 GB in size as minimum.
Next, once you have set the size, click create and your new virtual machine, with the configuration we have set, will be created. If you face any issues in getting the virtual machine on the network, then it is recommended to change the network configuration as follows.
Next, we are all set to install the Ubuntu Linux on this Virtual Machine we have just created. Follow the next step to install Ubuntu Linux. Go the settings and select the fresh downloaded copy of Ubuntu Linus ISO image to configure in the CDROM option so that you can boot from CDROM to install the Ubuntu Linux.
Next, start the virtual machine to run the Ubuntu Linux Operating System installation. It’s a very easy and self guided installation. However, we will still present the step-by-step guide so that you can quickly get through the installation.
Next, click install Ubuntu to follow the installation process.
Next, click continue to begin the installation.
Next, select erase disk and install Ubuntu and click install now.
Next, select your location, as I am from Auckland, New Zealand, hence, Auckland is my location; it is necessary to select the correct location so that your timestamp is not different. Continue to follow the installation process.
Next, select your English and click continue.
Next, set required details for your profile, your username & password and also the computer name & click continue and the installation will begin.
Next, sit back and relax until you see the below screen.
Confidentiality is satisfaction or assurance that the information that is supposed to be accessed by only a set of individuals is actually only accessible to those people.
Integrity is something which is accurate and unchanged and it’s the trustworthiness of the data or resources.
Availability is the assurance that the systems, applications or resources and data are actually available as required.
Vulnerability is generally defined as the weakness; it could be in the design, source of the application, and configuration in the information technology environment including people – processes – technologies.
Threat is a combination of vulnerability and the motivation factors. Threat is sometimes also defined as any circumstances or event that can lead to a disastrous situation.
Exploit is a malicious piece of software code that is written to gain illegitimate access to the information technology environment. Exploits are written to gain the motive by making use of weaknesses in the respective environment. It is simply designed as a way to breach the information security controls.
Payload is simply a part of an exploit; payload is the actual piece of code, which is written to perform specific tasks.
Zero-Day is an attack in which a hacker exploits the certain vulnerability before the launch of any patch from the vendor for this vulnerability.
Ethical hacking & Penetration Testing
Ethical hacking and penetration testing don’t have anything different in them and they are just two different terminologies presenting the same theory.
Penetration testing gathers the information about the actual attack footprint of your organization’s overall security, depending on the scope of the work.
In this workshop, we will talk about the 90/10 principle that we will cover in upcoming modules in more granular details.
A one line summary is “penetration testing is actual exploitation of vulnerabilities by means of ethical hacking”.
Virtual Lab Setup
We will be delivering a step-by-step guide to build your own lab so that you can practice the workshop at your desk. Lab requirements:
• Virtual Box Software
• Ubuntu Linux
• Nmap
• Nessus Home Feed
• NeXpose
• Metasploit Framework
• Vulnerable Operating System (Metasploitable)
Step 1 – Installing Virtual Box Software
Download Link: https://www.virtualbox.org/wiki/Downloads.
Select & download the binary, as per your operating system requirement. In my case, I will be installing the VirtualBox-4.3.12-93733-OSX from the above download link as shown below.
Next, double click the icon as shown in step 1 in above figure.
Next, continue to install by clicking the continue button.
Next, begin installation by clicking the continue button
Next, select the installation location or customize the installation as shown above, however, it is recommended to leave the settings as default and hit installation.
Next, successful installation will show the below screen.
Virtual box installation is now complete.
Step 2 – Installing Ubuntu Linux
We have successfully completed the installation of Virtual Box software. Now let’s install the Ubuntu Linux operating system to build the lab on top of Ubuntu Linux as Operating System. First we need to get the latest copy of the Ubuntu Linux Operating System. Based on your hardware architecture, you can select the ISO to download.
Download Link for Ubuntu Linux: http://www.ubuntu.com/download/desktop.
For your ease of access we have provided the above link for the downloading of Ubuntu Linux operating system and below is the snapshot of the said link.
We have successfully downloaded the copy of the Ubuntu Linux Operating System.
Next is setting up of Virtual Machine to run this Ubuntu Linux operating system. Let’s begin, starting the Virtual Box and follow the following sequential steps to setup a new virtual machine and install the Ubuntu Linux.
Next is creating a new virtual machine. In this step, we will name the virtual machine and set the type as Linux and the version as Ubuntu Linux (64-bit).
Next, click continue and follow the next step as shown below to configure the memory size for your new virtual machine. It is recommended to set the memory size as 1512 MB.
Next, click continue and follow the next step as shown below to configure your new virtual machine’s hard drive.
Next, click create and follow the next step to configure the hard drive file type. It is recommended to use VID as the file type for the hard drive.
Next, click the continue button and follow the next step to configure the storage on physical drive and it is recommended to dynamically allocate the memory.
Next, click continue and follow the next steps to allocate the hard drive file and size. It is recommended to keep the size as 26 GB in size as minimum.
Next, once you have set the size, click create and your new virtual machine, with the configuration we have set, will be created. If you face any issues in getting the virtual machine on the network, then it is recommended to change the network configuration as follows.
Next, we are all set to install the Ubuntu Linux on this Virtual Machine we have just created. Follow the next step to install Ubuntu Linux. Go the settings and select the fresh downloaded copy of Ubuntu Linus ISO image to configure in the CDROM option so that you can boot from CDROM to install the Ubuntu Linux.
Next, start the virtual machine to run the Ubuntu Linux Operating System installation. It’s a very easy and self guided installation. However, we will still present the step-by-step guide so that you can quickly get through the installation.
Next, click install Ubuntu to follow the installation process.
Next, click continue to begin the installation.
Next, select erase disk and install Ubuntu and click install now.
Next, select your location, as I am from Auckland, New Zealand, hence, Auckland is my location; it is necessary to select the correct location so that your timestamp is not different. Continue to follow the installation process.
Next, select your English and click continue.
Next, set required details for your profile, your username & password and also the computer name & click continue and the installation will begin.
Next, sit back and relax until you see the below screen.
We are now done with the installation of Ubuntu Linux operating system. We will now install the required tools that we willbe using in our upcoming modules in this workshop.
We will cover the other steps to equip your virtual hacking lab in the upcoming modules.
We will cover the other steps to equip your virtual hacking lab in the upcoming modules.