Setting up the Lab Environment
Introduction
In order to achieve our objective, we need a test environment where we can keep testing until we reach the end results. To achieve this, let’s first select the vulnerable application and set up our lab for research.
Lab Setup
• Downloading & Installing Virtual Box
• Installing Windows XP as a Virtual Machine
• Downloading Vulnerable Application from Exploit-DB
• Downloading and Installing Immunity Debugger & Mona.py
• Metasploit Framework (pre-installed with Kali)
Step 1: Downloading & Installing Virtual Box
Download Link: https://www.virtualbox.org/wiki/Downloads.
Select & download the binary, as per your operating system requirement, in my case I will be installing the VirtualBox-4.3.12-93733-OSX from the above download link as shown below.
Double click the icon as shown in step 1 in above figure.
Continue to install by clicking the continue button.
Begin installation by clicking the continue button.
Select the installation location or customize the installation as shown above, however, it is recommended to leave the settings as default and hit installation.
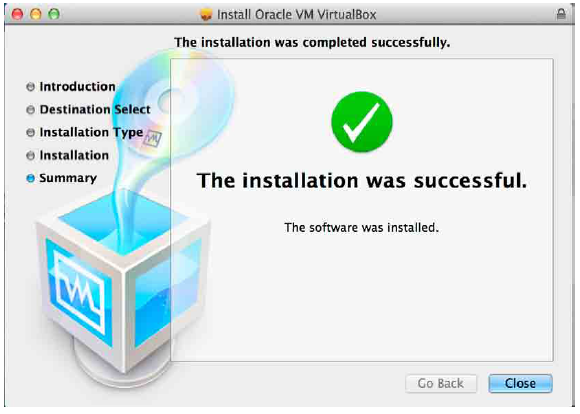
Successful installation will show the below screen.
Virtual box installation is now complete. Our next step will be setting up Windows XP as a virtual machine.
Step 2: Installing Windows XP as Virtual Machine
Let’s setup the Virtual Machine for Windows XP. The figures below explain the step-by-step method for configuring the new virtual machine by using Virtual Box.
Run the Virtual Box by simply clicking its icon from Applications and you will see it runs quickly, as shown below.
Click the new button on top left corner to setup new machine, type the name and select type of operating system and select the operating system version to install. Configure this as shown in below figure.
Once this is complete, you will be prompted to select the memory for this virtual machine.
Configure the memory size. As you are installing Windows XP, you do not need to waste your memory, 512MB of RAM size would be enough.
Next step is to configure the hard drive, for Windows XP 10GB space would be enough and is recommended.
Select the hard drive type as VDI (VirtualBox Disk Image) and continue.
Allocate the space dynamically to save your MAC machine.
Configure the size and name of the virtual hard disk you have just configured and create the disk as shown below.
Your new virtual machine is now complete. Once you create the hard disk, it will complete the setup of virtual machine and you will see the below outcome as shown in the figure.
Now it’s time to keep your Windows XP ISO image handy with you, as we will be installing Windows XP over this newly created virtual machine we have just finished with. Hit the settings button and you will be prompted with the following screen. Select the storage option.
In the storage Tree section, select Empty CDROM, as shown above, and you will see the following option. Click the CDROM button at the top right section, as shown below, to choose the Windows XP ISO image.
Once configured successfully, you will be good to install the Windows XP operating system into this Virtual Machine.
Now run the machine, sit back and install the Windows XP Operating System as you install it on the actual hardware, as shown below. Once this installation is completed, we will install the Vulnerable Application in Windows XP.
Without hiccups, this would lead to successful installation of Windows XP operating system. However, you need to ensure that your Network Card type is set as shown below in order to connect your Virtual Machine with your host operating system.
Network Card type should be set to PCnet-FAST III type, as shown in the below configuration.
Step 3: Downloading Vulnerable Application from Exploit-DB
So far so good, you have Windows XP running and connected with the Host machine and, as you can see in the above figure, we are able to reach the Internet. Let’s browse and look for the Free Float FTP Server from exploit-db.
You can Google around and see the below results to see if anything is available on exploit-db for the Free Float FTP Server.
Download the Vulnerable App from the below link.
Free Float Vulnerable Version: http://www.exploit-db.com/exploits/23243/.
It’s easy to install and run, as shown below, no further configuration is required to setup this vulnerable application.
Step 4: Downloading and Installing Immunity Debugger
To download Immunity Debugger, please follow the below link. You will be asked to register first in
order to download the Immunity Debugger.
Download Immunity: http://debugger.immunityinc.com/ID_register.py.
Installing Immunity Debugger on Windows XP. Run the downloaded setup file in order to install Immunity Debugger.
With the fresh installation of Windows XP, python is not available hence Immunity Installation will prompt you to install Python first, as shown above in the snapshot. Click yes and continue the installation setup.
Accept the license agreement and click next to continue the installation setup.
Select installing for all users, as shown in the above figure.
Leave the destination directory with the provided default settings and continue with your installation.
You are now finished with the installation of Immunity Debugger. Click the icon on your desktop to run Immunity Debugger for the first time.
We are finished with the Immunity Debugger installation, and now it’s time to plugin this debugger with the Mona.py plugin that we explained in previous module. You can download this plugin from the link below. Once the download is finished, simply place this Mona.py plugin file into the Immunity Installation folder and then PyCommands directory, as shown blelow.
Mona.py download link: http://redmine.corelan.be/projects/mona/repository/changes/mona.py?rev =master.
To ensure Mona.py is working, simply run Immunity Debugger and run the [!mona] command, as shown in the following figure. To run the command, type the command to run in the bottom text box and hit enter.
It’s now time to install Kali Linux same way as you have installed the Windows machine, the only difference is in selecting the Kali Linux ISO image.
You can also install Metasploit on the Windows XP we have just installed for this. Download the setup from rapid7 and installation is easy, as you have installed the Virtual Box in Windows XP. However, we will still take you through the installation of Kali Linux.
Step 5: Metasploit Framework (pre-installed with Kali)
Installing Kali Linux is easy, as we have explained above. Let’s quickly follow the steps shown below to install the Kali Linux.
Set up new machine as Linux Type, as shown below.
Continue the configuration of new virtual machine as BSD type.
Similarly, select the storage setting and select the Kali Linux Image as shown below.
Your Virtual Machine with the Kali Linux is now ready to boot from CD. We will recommend keeping the Live CD option for using on quick go.
Now let’s run and see if everything is configured successfully. You will be running two operating Systems side by side on your host machine.
Your lab is now up and running and configuration of the machines are as follows.
“Network Card type should be set to PCnet-FAST III type as shown in the below configuration”
Step 6: Lab IP Addressing
Host 1: Kali Linux
IP Address: 172.20.10.2
Host 2: Windows XP
IP Address: 172.20.10.14
FTP Server Listening on: 172.20.10.14
In the next module, we will be covering the basic skeleton of an exploit and how you can easily develop the exploit with the help of Mona.py.