Different Attack Vectors for Hacking Web Applications
Introduction
In this module, we will be focusing on the different types of attack, which can be targeted to web applications in order to compromise the web application and its underlying database or operating system.
If you are new to hacking, it is highly recommended than you should first complete the previous two modules and jump here to continue the workshop.
Types of Web Application Attacks
In this section of the module, we will try to cover most of the vulnerabilities that are usually found in the web applications. It is difficult to explain all of these in detail in a single module. However, we will try to present a basic idea of the background of the vulnerability covering what this vulnerability is used for and the short reason occasionally.
01 Default Login
One of the most common vulnerabilities found in web applications is the default login, which usually occurs due to the user and admin accounts developers create to test the application and then leave it unhardened.
02 Command Injection
A technique used by hackers to execute the system level commands by abusing the input features fields used for executable command to specific system calls in the web applications.
03 Local File include
This vulnerability allows the hacker to retrieve or execute server-side files. This vulnerability usually occurs due to not sanitizing the supplier user input and no access control mechanism implemented at the file level.
04 Remote Code Injection
A vulnerability that typically occurs due to the fact that application language allows dynamic execution of code at run time and attackers abuse the vulnerability to inject their code remotely into the application.
05 Remote File Include
A vulnerability that allows the hacker to manipulate the application in such a way that it allows the hacker to include a remote file hosted somewhere on the Internet server. Commonly, such files are executable in nature and typically written in a scripting language.
06 SQL Injections
The most common and most dangerous vulnerability, which is found in every other web application these days. This occurs due to not validating the input methods and badly written SQL statements inside the database layer of web applications.
The most common and most dangerous vulnerability, which is found in every other web application these days. This occurs due to not validating the input methods and badly written SQL statements inside the database layer of web applications.
07 Cross-site Scripting (XSS)
XSS is a type of web application security vulnerability that allows code injection by malicious web users into the web pages viewed by other users. However, this is only executable at the client side of the web application but sometimes it is found dangerous.
08 Weak Session Management
This vulnerability occurs when the web application produces a session cookie, whose value is easily guessable. For example, the session may be based on UNIX timestamps or just an MD5 of a timestamp, etc.
09 LDAP Injection
LDAP Injection is a Code Injection technique used against applications, which construct LDAPb statement based on user input. LDAP is an application protocol used to access and maintain distributed directory services, like Microsoft’s Active Directory.
10 Persistent Cross-Site Scripting (XSS)
Type of client side web application vulnerability allowing the hacker to inject the code at client side of the application into the web pages viewed by other users.
11 Cross-Site Request Forgery (CSRF)
Type of web application vulnerability in which an end-user is forced to execute the unnecessary or unwanted action on a web application resulting in leak of data.
We have listed the types of vulnerabilities that are commonly found in the web applications. Out of these vulnerabilities, we will explain in more granular details the most dangerous and high-risk vulnerabilities due to which most of the web applications are compromised.
High Risk Vulnerabilities
Web application vulnerabilities we have discussed so far were a mixture of low and high-risk vulnerabilities in general. Here we will only be discussing a couple of high risk vulnerabilities to give you a more narrowed and focused picture of the vulnerabilities you need to understand thoroughly and practice more in order to be good at performing web application security testing or an ethical hacking, which is also known as penetration testing.
Structured Query Language (SQL) Injections
Security researchers categorize SQL injection vulnerabilities as high risk in any web application vulnerability testing. This is a mechanism or a technique used by malicious users, termed as hackers, to break the web applications database layer security and steal the information which they are not supposed to access. Most of the web applications, including the enterprise organization’s web applications, have been hacked and defaced by hackers by the use of SQL injections.
This vulnerability exploits the database layer of the web application but it occurs at the application layer and takes advantage of the badly written code of web applications, giving an opportunity to hackers for executing the SQL injections.
[SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the application layer to the application server via database layer. In this way, you inject the query written in SQL statement to exploit another query written by the developer.]
To understand the SQL injection you first need to understand the structured query language in more detail. Let us first give you a quick intro of SQL statements.
The dynamic web application (if you don’t understand the types of web applications, it is recommended to go through the previous modules and clear the concepts of server and client side web applications) usually serves features like:
• Login-pages
• Product-request forms
• Feedback forms
• Search pages
• Shopping carts
• General delivery of dynamic contents
• Forums
• News Searches
• Search with the Primary ID in the database
• Admin Panels
• Product-request forms
• Feedback forms
• Search pages
• Shopping carts
• General delivery of dynamic contents
• Forums
• News Searches
• Search with the Primary ID in the database
• Admin Panels
• Dynamic Product Details Pages
• Dynamic Customer Details
• Dynamic Customer Details
Such website features are all examples of web applications which may be either purchased off-theshelf or developed as bespoke programs. Such features are basically based on the structured query language (SQL) in the background.
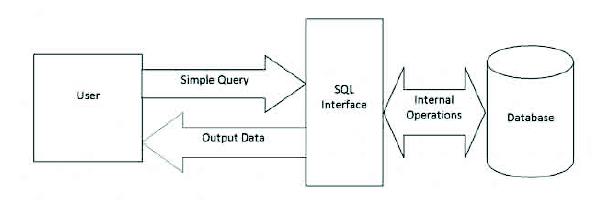
Basically, SQL is nothing but an interface, which connects you to the backend database where all the information is stored and is static in nature. Now, in order to perform any action on this static data sitting in the back end database server, we need to simply ask the database server to provide us the required information. This method of querying the database server is an independent method or you can say it’s a set format on which you need to raise queries to the database server.
This set format is your SQL interface in the form of a bunch of well-formatted statements known as SQL statements, which assist you in communicating with the database server and performing the required tasks you need to perform with the database server. Let’s have a quick look at the mechanism we have explained.
When users come to the dynamic or server side web applications, they have a purpose to achieve; users query the web application which is translated into the SQL statement which goes to the backend database and the database provides the required info or performs the tasks executed by the user in the form of SQL statements. The action, which is taken by the database server, is dependent on the statement it retrieves from the database layer, i.e. your SQL interface, which generates statements based on the user request.
Important Types of SQL Statements
Below are some of the important SQL statements that you should understand thoroughly from a web application security standpoint. To understand and take a deep dive into the below statements, you should focus yourself on a short SQL course, as covering these in detail here is not our objective.
However, we will present a couple of attack vectors in SQL injections so that you can have an idea how dangerous SQL injections are.
• SELECT – extracts data from a database
• UPDATE – updates data in a database
• DELETE – deletes data from a database
• INSERT INTO – inserts new data into a database
• CREATE DATABASE – creates a new database
• ALTER DATABASE – modifies a database
• CREATE TABLE – creates a new table
• ALTER TABLE – modifies a table
• DROP TABLE – deletes a table
• CREATE INDEX – creates an index (search key)
• DROP INDEX – deletes an index
• UPDATE – updates data in a database
• DELETE – deletes data from a database
• INSERT INTO – inserts new data into a database
• CREATE DATABASE – creates a new database
• ALTER DATABASE – modifies a database
• CREATE TABLE – creates a new table
• ALTER TABLE – modifies a table
• DROP TABLE – deletes a table
• CREATE INDEX – creates an index (search key)
• DROP INDEX – deletes an index
Example & SQL Injections Exploitations
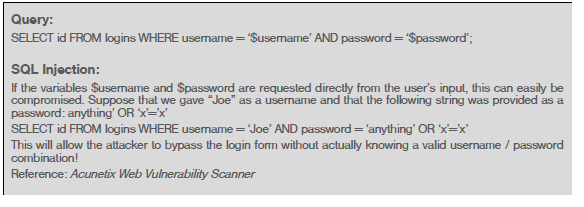
Example 1: Login Bypass SQL Injection
Example 2: SQL Injection Union Attack
Union attack is one of the most common and a bit of a complicated type of SQL injection. It is not easy to inject the union attack, however, if you succeed in running this attack, then the damage is high.
Example 3: Command Injection Vulnerability
Command execution vulnerability is executed and explained below. Here we will execute this and present different ways to grab more information from the web server. Considering this web application is built to provide a service of [ping], we will try to execute other commands and grab more information. Legitimate use is when we ping www.yahoo.com from the ping box as shown below in the snapshot.
Since this application is badly coded, an attacker can make a good use of this badly written code by means of running other system level commands. Let’s try to run a command in combination with the legitimate command to grab more information.
We injected the system command to see the Internet addresses configured on this web application server and below is the snapshot to confirm the successful execution.
As this application was not validating the input, hence, we succeeded in exploiting the web application with a command injection attack.
Summary
The Web Application hacking techniques we have discussed in this module don’t cover everything in the circle of hacking into web applications, however, we have presented the overall techniques most commonly used to compromise the web applications.
By using the technique explained in this module, you will be able to take advantage of SQL injection and command injection vulnerabilities in order to perform ethical hacking for web applications