WIRELESS HACKING WITH AIRCRACK-NG
Introduction
Given our increasing need to stay connected via social media, email and, therefore, have access to the Internet, the availability of free, open WiFi access points in institutions, shops and in some areas, city-wide access points has become the norm. We don’t give a second thought to accessing a free WiFi spot in a coffee shop or otherwise since it enables us to maintain access. But, what about our home? While you may have followed our best advice to select a password for your router, implemented WPA/WPA2 encryption, it is possible, with help, to access these also. In this
article, we outline the use of a tool called ‘Aircrack-ng’ used by security professionals to access secured WiFi.
Cracking WEP Versus WPA
The approach used to crack the WPA/WPA2 pre-shared key versus WEP differ significantly. WEP can leverage statistical methods to speed up the cracking process, however, only brute force techniques will work against WPA/WPA2. In WPA/WPA2, the key is not static, so collecting (initial vectors) IVs (unlike WEP) does not speed up the attack. The handshake between the access point and the attacker does reveal some information, though, when handshaking is connecting a client to a network. It should be noted that a pre-shared key can be from 8 to 63 characters in length, making is impossible to crack the pre-shared key (Aircrack-ng, 2010).
Authentication is basically the same between WPA and WPA2. The objective is to capture the WPA/WPA2 authentication handshake and then use aircrack-ng to crack the pre-shared key.
Cracking WEP encryption
WEP, or Wired Equivalent Privacy, is an 802.11 standard used for encryption in Wireless LANs (IEEE, 2012). WEP has two main functions, ensuring that traffic cannot be viewed by untrusted parties and preventing unauthorized access to a network. The algorithm itself uses the RC4 cipher and 64-bit/128-bit keys to encrypt and decrypt and ensure the integrity of the packets. Weaknesses in the key scheduling of the RC4 algorithm (Fluhrer, Mantin, & Shamir, 2001) were first identified in 2001. Although RC4 is still secure when used with recommended methods, the researchers discovered that when using RC4 with WEP that it is significantly weakened. WEP’s flaws include lack of packet replay protection, weak packet integrity checks and the fact that it is possible to recover the key from a collection of captured packets. Each WEP packet must be sent with a 4-byte header containing a one byte index number and a three byte IV. WEP key recovery relies on capturing a large number of unique IV values.
Steps to Crack Wireless Signals using Aircrack-ng
Aircrack-ng offers a lot of helpful steps to use their tool. The first step is to start the wireless interface in monitor mode (Aircrack, 2010) so put your card into what is called monitor mode. Monitor mode is the mode whereby your card can listen to every packet in the air. Normally, your card will only “hear” packets addressed to you.
We can see in the example above that there is one wireless adapter called ‘wlan0’ associated with the physical interface phy0. Next, we place this interface in ‘monitor mode’, simply run the command,
The airmon-ng tool will create a monitor mode interface associated with the physical device used by the interface with the name mon0.
The next step is to select a suitable access point (AP) or router from which to capture traffic. This can be done using the Airodump-ng script with the specified interface.
The field that we are most interested in is Data or IV, as discussed, but many IVs are required. Once the AP has been identified, the next step is to capture the packets and place them in a file for analysis. We use Airodump-ng, specifying the channel, file to write to and the interface.
Although the frames are being captured we need to speed up the process because we need a large amount of IVs, and this can be done by performing an ARP replay attack.
Once the attack is initiated, the data/IV column will rise at a much quicker rate. A combination of aircrack-ng and the capture file may now be used to launch the attack.
If the program does not have enough IVs, this may take repeated attempts. A successful crack will return the password in hex form.
Cracking WPA-PSK encryption
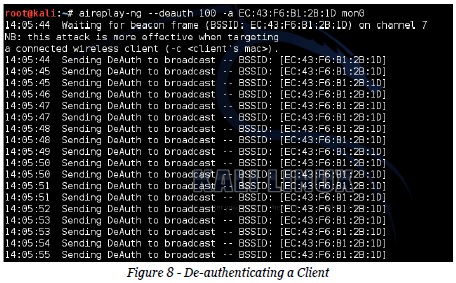
This time, instead of trying to increase the data (IVs) in the WEP cracking the objective is to achieve a 4-way handshake. It should be noted that in order for this attack to work, at least one client needs to be connected. The reason for this is that to create a 4-way handshake the client needs to be first disconnected and then reconnected.De-authenticating a client is done using,
In this case, we brute force the password with aircrack-ng in combination with a password list.
A penetration tester would use a combination of dictionary, mutated and compromised password lists.
Conclusion
As useful as the Aircrack-ng tool is in cracking wireless signals, it is a job that requires some patience and technical ability and ultimately, if the password is not in your dictionary, it will not be found by Aircrack-ng either. Therefore, the best advice is to select a better password or, better yet, passphrase.
What you will learn
How to use the Aircrack-ng tool.
Aircrack-ng is a widely used tool with capabilities to crack WEP and WPA.
Given our increasing need to stay connected via social media, email and, therefore, have access to the Internet, the availability of free, open WiFi access points in institutions, shops and in some areas, city-wide access points has become the norm. We don’t give a second thought to accessing a free WiFi spot in a coffee shop or otherwise since it enables us to maintain access. But, what about our home? While you may have followed our best advice to select a password for your router, implemented WPA/WPA2 encryption, it is possible, with help, to access these also. In this
article, we outline the use of a tool called ‘Aircrack-ng’ used by security professionals to access secured WiFi.
Cracking WEP Versus WPA
The approach used to crack the WPA/WPA2 pre-shared key versus WEP differ significantly. WEP can leverage statistical methods to speed up the cracking process, however, only brute force techniques will work against WPA/WPA2. In WPA/WPA2, the key is not static, so collecting (initial vectors) IVs (unlike WEP) does not speed up the attack. The handshake between the access point and the attacker does reveal some information, though, when handshaking is connecting a client to a network. It should be noted that a pre-shared key can be from 8 to 63 characters in length, making is impossible to crack the pre-shared key (Aircrack-ng, 2010).
Authentication is basically the same between WPA and WPA2. The objective is to capture the WPA/WPA2 authentication handshake and then use aircrack-ng to crack the pre-shared key.
Cracking WEP encryption
WEP, or Wired Equivalent Privacy, is an 802.11 standard used for encryption in Wireless LANs (IEEE, 2012). WEP has two main functions, ensuring that traffic cannot be viewed by untrusted parties and preventing unauthorized access to a network. The algorithm itself uses the RC4 cipher and 64-bit/128-bit keys to encrypt and decrypt and ensure the integrity of the packets. Weaknesses in the key scheduling of the RC4 algorithm (Fluhrer, Mantin, & Shamir, 2001) were first identified in 2001. Although RC4 is still secure when used with recommended methods, the researchers discovered that when using RC4 with WEP that it is significantly weakened. WEP’s flaws include lack of packet replay protection, weak packet integrity checks and the fact that it is possible to recover the key from a collection of captured packets. Each WEP packet must be sent with a 4-byte header containing a one byte index number and a three byte IV. WEP key recovery relies on capturing a large number of unique IV values.
Steps to Crack Wireless Signals using Aircrack-ng
Aircrack-ng offers a lot of helpful steps to use their tool. The first step is to start the wireless interface in monitor mode (Aircrack, 2010) so put your card into what is called monitor mode. Monitor mode is the mode whereby your card can listen to every packet in the air. Normally, your card will only “hear” packets addressed to you.
‘airmon-ng’
By hearing every packet, we can later capture the WPA/WPA2 4-way handshake. As well, it will allow us to optionally deauthenticate a wireless client in a later step. The airmon-ng tool that comes packaged with the Aircrack-ng suite of tools can be used to place a wireless adapter into monitor mode. To identify the wireless cards on the system run the airmon-ng command with no arguments.We can see in the example above that there is one wireless adapter called ‘wlan0’ associated with the physical interface phy0. Next, we place this interface in ‘monitor mode’, simply run the command,
‘airmon-ng start wlan0’
The next step is to select a suitable access point (AP) or router from which to capture traffic. This can be done using the Airodump-ng script with the specified interface.
‘airodump-ng’
Airodump-ng provides a great deal of information described in the table below:
Although the frames are being captured we need to speed up the process because we need a large amount of IVs, and this can be done by performing an ARP replay attack.
Once the attack is initiated, the data/IV column will rise at a much quicker rate. A combination of aircrack-ng and the capture file may now be used to launch the attack.
If the program does not have enough IVs, this may take repeated attempts. A successful crack will return the password in hex form.
Cracking WPA-PSK encryption
This time, instead of trying to increase the data (IVs) in the WEP cracking the objective is to achieve a 4-way handshake. It should be noted that in order for this attack to work, at least one client needs to be connected. The reason for this is that to create a 4-way handshake the client needs to be first disconnected and then reconnected.De-authenticating a client is done using,
‘aireplay-ng’
With a successful WPA handshake the top right of the airodump-ng terminal looks like below,
‘aircrack-ng –w wordlist name-01.cap’
Conclusion
As useful as the Aircrack-ng tool is in cracking wireless signals, it is a job that requires some patience and technical ability and ultimately, if the password is not in your dictionary, it will not be found by Aircrack-ng either. Therefore, the best advice is to select a better password or, better yet, passphrase.