Linux Basics and Command Line
Introduction
Welcome to the Module 2 of this workshop. So far in this workshop, we have talked about GCC & GDB and Ubuntu Linux setup. Linux is basically an open source operating system which s based on the Unix platform. However, Linux is now a much more enhanced, strong, fast and much more reliable operating system, which steps ahead of the Windows platform.
In this module, we will explore Linux and its different flavors. We will be learning different techniques and commands that you should know in order to use Linux as a normal user, at minimum.
PreRequisite
Since we will be learning about Linux knowledge base, this module doesn’t require any prerequisites, especially on Linux, however, you should be a computer user and have prior experience with DOS.
Linux Key Components
It is very difficult to completely cover all Linux components aspects in one workshop, however, we will be presenting the overall overview here on the Linux components side.
Basically, Linux operating system has three primary components:
• Kernel – Kernel is the core part of Linux. It is responsible for all major activities of this operating system. It consists of various modules and it interacts directly with the underlying hardware. Kernel provides the required abstraction to hide low-level hardware details from system or application programs.
• System Library – System libraries are special functions or programs that use application programs or system utilities to access the Kernel’s features. These libraries implement most of the functionalities of the operating system and do not require kernel module’s code access rights.
• System Utility – System Utility programs are responsible for performing specialized, individual level tasks.
The diagram below provides the overall design view of Linux components.
• Hardware layer – Hardware consists of all peripheral devices (RAM/ HDD/ CPU, etc.).
• Kernel – Core component of the operating system, interacts directly with hardware, provides low level services to upper layer components.
• Shell – An interface to the kernel, hiding the complexity of kernel’s functions from users. Takes commands from user and executes kernel’s functions.
• Utilities – Utility programs giving user most of the functionalities of an operating system.
Following are some of the important features of Linux operating system:
• Portable – Portability means software can works on different types of hardware in the same way. Linux kernel and application programs support theiinstallation on any kind of hardware platform.
• Open Source – Linux source code is freely available and it is a community based development project. Multiple teams work in collaboration to enhance the capability of Linux operating system and it is continuously evolving.
• Multi-User – Linux is a multiuser system, meaning multiple users can access system resources, like memory/ RAM/ application programs, at the same time.
• Multiprogramming – Linux is a multiprogramming system,meaning multiple applications can run at the same time.
• Hierarchical File System – Linux provides a standard file structure in which system files/ user files are arranged.
• Shell – Linux provides a special interpreter program which can be used to execute commands of the operating system. It can be used to do various types of operations, call application programs, etc.
• Security – Linux provides user security using authentication features, like password protection/ controlled access to specific files/ encryption of data.
So far in this workshop we have systematically talked about some of the basic things about Linux Operating system and we have covered its architecture, components and some key features. Linux has a powerful mechanism by which you interact with Linux. This interface is basically Linux Shell Command Interpreter.
Linux Shell
The shell command interpreter is the command line interface between the user and the operating system. It is what you will be presented with once you have successfully logged into the system.
Linux Shell allows you to enter commands that you would like to run, and also allows you to manage the jobs once they are running. The shell also enables you to make modifications to your requested commands.
Different types of Shell
The Bourne-Again shell is not the only shell command interpreter available. Indeed, it is descended from the Bourne Shell (sh), written by Steve Bourne of Bell Labs. This shell is available on all Unix variants, and is the most suitable for writing portable shell scripts.
Default Shell (Bash)
The default shell, which is provided with most Linux based systems, is the Bourne-Again shell (“bash”).
Other popular shells include the C Shell (csh), written at UCB, and so called because its syntax is similar to that of the C language.
However, the TC Shell (tcsh) is an extension of the C shell.
A very popular shell on most commercial variants of Unix is the Korn Shell. Written by David Korn of Bell Labs, it includes features from both the Bourne shell and C shell.
Last, but not least, one of the most powerful and interesting shells, although one that hasn’t been standardized on any distribution that I’ve seen, is the Z shell. The zsh combines the best of what is available from the csh line of shell utilities as well as the best that is available from the Bourne or bash line of shell utilities.
Linux File System
Each disk drive in a Linux Operating System can contain one or more file systems. A file system consists of a number of cylinder groups, which in turn contain inodes and data blocks.
In Linux, each file system has its characteristics described by its “super-block”, which in turn describes the cylinder groups. A copy of the super-block is made in each cylinder group, to protect against losing it. Basically, a file is uniquely identified by its inode on the filesystem where it resides.
What is Data Block?
A data block is simply a set block of space on the disk in which the actual contents of files are stored; often, more than one block is used to hold the data for a file.
What is Inodes?
An inode is a data structure that holds information, or metadata, about a file on that file system. You can use “ls” with the “-i” option to find a file’s inode number:
Linux File System Layout
Linux File System Hierarchy
The Linux file system is broken up into a hierarchy similar to the one depicted below, of course, you may not see this entire structure if you are working with the simulated Linux environment, however, the below presented layout is the general level layout which is considered as universal structure.

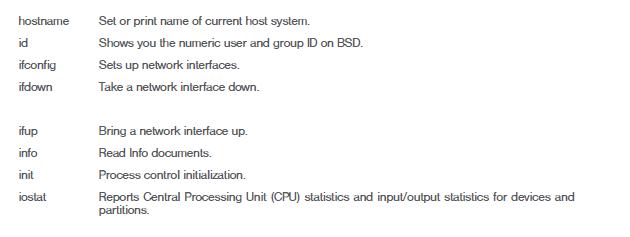
Some Linux Commands and their usage
The Linux operating system has evolved a lot and you can easily find many of the Linux flavors that provide an awesome GUI for your ease of use, however, there is still a need for understanding how Linux works over command line.
There are thousands of Linux commands that you can easily find on the Internet when you need to use them, however, we will present commands that you might require in this workshop and a few more of them.