Setting up your Virtual Environment
Welcome to the first module of this workshop where we will present lots of hacking tricks and techniques you can achieve with Kali Linux. In fact, you can perform complete end-to-end hacking with Kali Linux. When thinking about hacking you might think that it’s a difficult job, but with Kali, this job will be much easier and all the instructions will be presented in this workshop.
Prerequisites
Surprisingly, you don’t need to have any solid background in a security or hacking field, we will present all the skills that can make you a hacker!
However, you need to have a solid playground where you can perform hacking on a trial basis and for this reason you need to have a solid machine on which you can build your hacking environment. In this module, we will be guiding you on how you can make your own lab to practice hacking.
Building the Virtual Hacking Environment
To achieve this goal, you need to have one platform on which you can run multiple operating systems including victim machines and Kali Linux as your master machine from which you will be performing hacking attempts. To make it happen, let’s download Virtual Box!
Download Link: https://www.virtualbox.org/wiki/Downloads.
Now select & download the binary, as per your operating system requirement, in my case, I will be installing the VirtualBox-4.3.12-93733-OSX from the above download link as shown below.
Great, Virtual Box installation is now complete. This will be your platform on which you will be building the virtual lab to learn hacking with Kali Linux.
Now we will proceed with installing Kali Linux. First we need to get the latest copy of the Kali Linux Image from kali.org.
Download link: http://www.kali.org/downloads/.
Download the Kali Linux image as per your hardware requirements; in our lab, we will be using Kali Linux 64 bit ISO 1.0.0 version.
Once you finish the download then follow the below steps to prepare the virtual machine in order to install the Kali Linux on top of it.
Setup up virtual machine and install Kali Linux (master operating system)
Following the instructions as shown for installing Kali Linux.
Now set up new machine as Linux Type, as shown below, and continue the configuration of a new virtual machine as BSD type.
Now your Virtual Machine with the Kali Linux is running as shown above to boot from CD in shown modes of Kali Linux. We recommend keeping the Live CD option for using on go. However, you can choose options to install the Kali Linux as Operating System.
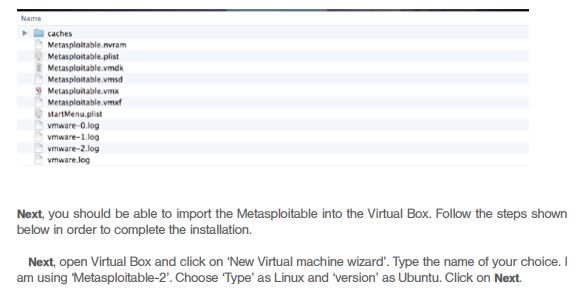
Great, you managed to install Kali Linux but this is just the one side of the mirror, as you also need the victim machines that you can hack into by using Kali Linux. For this purpose we have the following options to build the next requirements of our virtual hacking lab.
1. Vulnerable Microsoft Operating System (Windows XP)
2. Metasploitable (Linux as Vulnerable Operating System)
3. Vulnerable Microsoft Operating System (Windows 8)
We will setup these above vulnerable operating systems in our environment so that we can practice with real hack attempts.
Also, it’s beneficial to install two instances of each operating system, however, think about your hardware capacity, as well.
Victim Machine (Microsoft Windows)
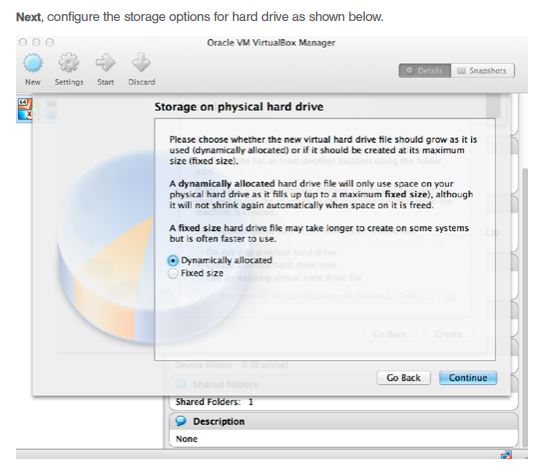
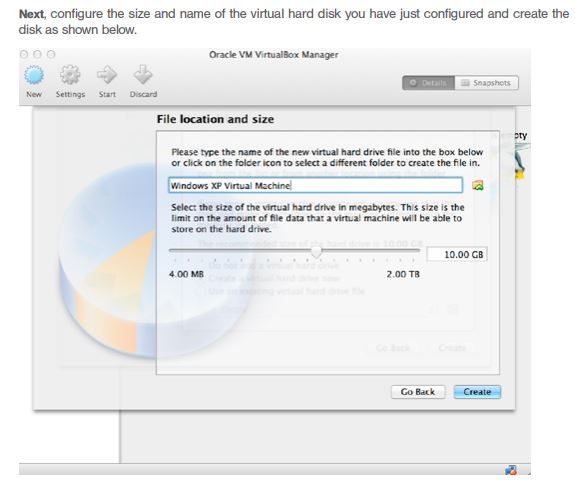
Now setup up a new machine as shown below to install Windows XP with the following naming and type info.