Demo Code Review
Introduction
Welcome to the fourth module of software security testing workshop. In this workshop so far we have spoken enough about security testing in software code, methodologies and different types of software testing along with different tools introduction that are available easily in the industry market. However, so far we have not presented a practical demo for performing code review.
This will be a quick module to demonstrate how you can perform code reviews before you put your code on a live desk. We will be using Flawfinder as our tool to review code written in “C” language.
What is Flawfinder?
The Flawfinder is an open source security code review tool that is easily available to be downloaded from the Internet in one quick go.
Vendor’s mouth
“A simple program that examines C/C++ source code and reports possible security weaknesses (“flaws”) sorted by risk level. It’s very useful for quickly finding and removing at least some potential security problems before a program is widely released to the public, Flawfinder is specifically designed to be easy to install and use.”
How does it work? Flawfinder works by using a built-in database of C/C++ functions with well-known problems, such as buffer overflow risks like:
• strcpy()
• strcat()
• gets()
• sprintf()
• scanf() family.
It also detects format string problems such as
• [v][f]printf()
• [v]snprintf()
• syslog()
Race conditions such as
• access()
• chown()
• chgrp()
• chmod()
• tmpfile()
• tmpnam()
• tempnam()
• mktemp()
Potential Shell met character dangers (most of the exec() family, system(), popen()), and poor random number acquisition (such as random()).
The good thing is that you don’t have to create this database – it comes with the tool.
Easy to use
Flawfinder is extremely easy to use, and doesn’t require long hours and dependencies before its installation. It is a Linux based product and you can easily install this on Kali Linux as part of your security testing Swiss army knife.
Download: http://www.dwheeler.com/flawfinder/flawfinder-1.31.tar.gz.
We will present quick installation steps so that you can setup your machine, as well, however, it doesn’t take much time, honestly.
Login to your Kali Linux and open up terminal windows and you can download this via above direct link as shown below in the figure.
You can directly use Flawfinder from this directory, however, it’s worthwhile if you can install this by using the following commands as shown in the figure so that you can more easily use Flawfinder.
Practicing Flawfinder We have downloaded sample “C” codes from the Internet that are easily available with a search over Internet. Now it’s time to run some quick reviews with Flawfinder. We have the following “C” files available in a directory called scripts as shown in below figure.
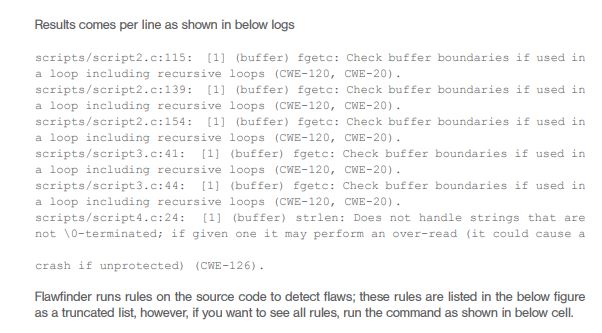
You can see that Flawfinder has detected 183 hits. These hits are potential vulnerabilities Flawfinder has detected. The total time it took is less than 1 second, a rate of 49579 lines / second, and the total lines it reviewed was 3392.
The steps Flawfinder performs are given below as captured logs: