Walkthrough on Hacking Databases
Case Study on Manually Hacking Web
Applications
Welcome to the third module of the “Database hacking workshop”. In this
module, we will have walkthroughs on hacking databases with techniques
that will show you how to hack into web applications and compromise
backend databases.
We will cover SQL Injections (SQLi) that we studied in the previous
module by practicing them on vulnerable web applications with the realtime SQLi testing we are executing in our lab environment. Information
that can identify any sensitive information will be marked as such,
however, we will help you understand this and in later modules we will
also explain how you can setup a lab to practice these skills and gain
more experience.
Okay, now have a quick flash back and remember the SQLi we studied in
previous module; we explained one SQLi type, authentication bypass, with
a walkthrough on a web application. Here we will study more with other
types of SQLi so that we cover those types as well.
Let’s begin with another type of SQLi; we will first do “union attack”.
Union Attack SQLi
As we studied in the previous module, this type of SQLi in its simple form
can be explained as appending another select query as SQLi. However, it’s
not that easy to do because to execute another statement as union, you
need some information prior to executing this type of SQLi attack. So first,
let’s have a look at how you can detect the SQLi attack. Consider the
below link as our target link to perform a SQLi attack.
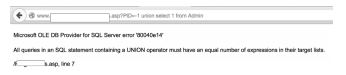
SQLi: SomePage.asp?PID=1
Now, we will try to generate some errors by providing bogus information
instead of PID=1 as shown in below link and will see what error occurs.
SQLi: SomePage.asp?PID=-1
We typed “-1” instead of [1] which gives us the following error as shown
below in the figure.
Notice the UNION SQL statement we appended after “-1” id as value and
then we injected the union statement as our SQLi.
However, since we don’t know column and table names, so we simply said
select first column from table “news”. Since the news table doesn’t exists
in the current database, the SQL server gives an error that “news” is an
invalid object name, which means table “news” doesn’t exist. However,
we now are confident that union attack may work here.
So what we need to know first is a valid table name in the database.
Usually, programmers create set table names, like “admin” for admin login table, users table for storing user related information, which could
be anything, and so on. Since we are doing it manually, we have to guess
and give a try again. Let’s say table name “Admin” and see what happens.
Aha, you can see that now we have been given more information by this
vulnerable application and we can see that message is changed from
invalid object to the SQL specific message that:
“All queries in an SQL statement containing a UNION operator
must have an equal number of expressions in their target lists”
This means that the SQLi we are performing as a union query attack
should have equal number of expressions, like column names, which also
means that table “Admin” does exist in the database but the number of
columns are different than the table from which the first SQL statement
was written by the programmer to get the data from the database onto
this web page.
So now we have a valid table name with us, that is “admin” but we still
cannot execute the UNION attack, as we don’t have the columns
information. So let’s work to learn more information about the columns.
How we do this is we keep adding column numbers until we see a
different error which ends up in the following union attack query.
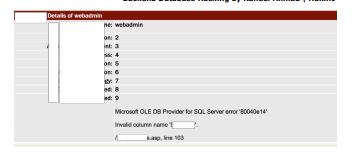
SQLi: SomePage.asp?PID=-1 union select
1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16 from Admin
And we landed on the below page with following information as shown
below in the snapshot. Information is anonymized for privacy reasons.
Cool, this means that we were able to execute our SQLi union attack to an
extent that gives us information as shown in above snapshot. Now let’s
read this information.
You can see the numbering from 1 to 9 and then an error message by
SQL Server. This shows that you can read what is there in the first 9
columns of table “admin” on the page you landed on after this SQLi
attack.
But, you need to know column names if you want to read information
from the table “admin” which you can use instead of numbers from 1 to 9.
So let’s start with common guessable column names that any programmer
can use. Think like a programmer. We will start with “username” as the
first column name and will see what happens.
So our SQLi union attack query would look like this as given below.
SQLi: SomePage.asp?PID=-1 union select
username,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16 from Admin
However, when we executed this attack, we saw the following error
message again by the SQL server as shown below in the snapshot.
Which means no column exists as “username” so our bad luck here, no
worries let’s try with “user” and see what happens. Now our SQLi attack
query would look like this as shown below.
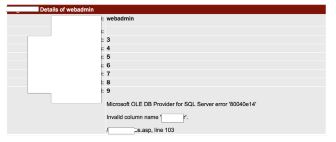
SQLi: SomePage.asp?PID=-1 union select
user,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16 from Admin
When we executed things could change and we land on the following page
as shown below.
Cool, this means that we got the correct column name as we placed it in
the first place as you can see that now we can put some text in the same
location where we displayed number 1 and this text “webadmin” is
basically a user name and the username itself says it’s a web
administrator account. So we are hacking into the web application.
However, we need to know the password, so apply the same logic to find
out the password column with different column names.
So long story short, we tried different names and found that “pwd” is
probably the column that has passwords, however, for this user no
password was set. The SQLi attack query we sent was as given below.
SQLi: SomePage.asp?PID=-1 union select
user,pwd,3,4,5,6,7,8,9,10,11,12,13,14,15,16 from Admin
And, we got the following information as shown below in the snapshot.
As you can see, now there is blank field on location 2. So what did we
learn here?
A successful union attack and information gathering on registered users,
so we can try gathering more information from any other known tables.
This you have to do on your own, however, we can confirm that we found
more table names including “user”.
We will now cover Blind SQLi Attack in the next walkthrough and hope
that you got the grip over union attack. This union attack can be extended
further but that we can not cover in this workshop. If you want to learn
more on extended attack methods, request a separate workshop on
advanced and extended SQL Injection attacks and we will arrange it for
you.
Tutorial 2 – Quick Walkthrough on Blind SQL Injection Attack
Cool, we have studied union attacks and authentication bypass attacks
with walkthroughs now let’s quickly learn blind SQL injection. We have
explained the concept in a previous module, however, let’s have a look at
the SQLi blind attack queries we can use in any blind SQL injection
attacks. Keep in mind that this is an attack type which is sort of your last
resort so we will not be diving deep here but just to give you an idea.
As you learned, table names and column names guessing is going to take
time and sometimes it’s not easy to guess with directly hitting names,
however, you can construct the names by using this SQLi attack with the
query as shown below.
SomePage.asp?id=1 AND ISNULL(ASCII(SUBSTRING(CAST((SELECT TOP
1 LOWER(name)
FROM sysObjects WHERE xtYpe=0x55 AND name NOT IN(SELECT TOP 2
LOWER(name) FROM sysObjects WHERE xtYpe=0x55))
AS varchar(8000)),1,1)),0)=97
What happens here is that it will guess the first character of the second
table name in the database, however, this will take more and more time
and the results will take much effort but this type of attack does help you
in situations where you can’t do any other type of SQLi attacks.
Why not play with something where you get more room to find more and
more information in bulk? And easily hack into web application and
completely comprise the backend database? Sort of like dumping
everything available in the backend database? This may sound bit weird
as well as difficult to you but it all depends on how you perform SQLi
attacks and what type of attacks you are performing.
But, this is possible and that is why we are studying something that is
doable, however, this is not possible with Blind SQLi. You need to do
something else so let’s have another walkthrough and see how this is
achievable.
Walkthrough on Compromising Backend Database with SQLi Attack
Okay, cool. Get ready to read everything available in the backend
database by exploiting the SQLi vulnerability. But how is this possible? In
our current penetration testing we are performing we found another page
with SQLi attack which is a search field having an SQLi vulnerability. This
type of SQLi vulnerability gives you more room to dump all database
contents.
But, some pre-requisite knowledge is a must in such SQLi attacks, since
we are attacking on MSSQL Server running in backend, we must know
enough about its default features and views and how MSSQL operates.
However, since we are not in a database course but a hacking course,
which definitely requires enough knowledge on the system you are trying
to hack. To gain such knowledge and learn about these features of SQL
Server we recommend that you should build your knowledge base by
going through the following MSDN link so that you understand what will
be happening here in the SQLi attack.
External link: https://msdn.microsoft.com/en-us/library/ms177596.aspx
To accomplish this we will again use the union operator but at an
advanced level by using the default features of SQL Server as explained in
the above link. So how to execute this.
We know vulnerable page, what we need is the number of columns in the
SQL Statement written in background by programmer so the number of
column matches in UNION attack.
Advance SQLi Attack
This advanced level of SQLi attack we will be performing will require SQL
Server views to be used, let’s see how it works. The below query was
executed successfully in a search field as shown in below snapshot on a
different page of the web application.
Advance SQLi Attack: union select 1,2,3,4 from sysobjects;--
This SQLi attack took us to search page and we go to the below screen as
shown in snapshot.
The logic behind these numbers from 1 to 4 we have already explained,
now the fun will begin when we will use two column names of this
sysobject table available as default in the SQL Server. So let’s try and
provide two column names we know which are “id” & “name” since this is
a default view so we know it by default and you can practice by going into
it as we explained in previous modules.
So after adding these two column names our SQLi would look like as given
below.
Advance SQLi Attack: ' union select id,name,3,4 from sysobjects;--
When we executed this SQLi the search works well and took us to the
following page as shown below in the snapshot and you can see what we
have discovered.
Now the first column is the “ID” of this table and second column is the
“name” of the table so now we can find available columns in any table, we
will select one to demonstrate.
We selected two IDs from the above list, one of the default table and one
from user defined table as shown in below SQLi
Advance SQLi Attack: ' union select id,name,3,4 from syscolumns
where id=1125579048;--
Advance SQLi Attack: ' union select id,name,3,4 from syscolumns
where id=10;--
And we found the below information for each query, respectively.
Similarly, you can execute more advanced and customized queries to read
through databases and dump all the content.
We hope you learned something new today and enjoyed the workshop
and want to hack into databases yourself so let’s help you in setting up
your home lab for practicing the gained knowledge.
We hope it’s beneficial for your career and thank you for attending the
workshop.