Tutorial 1 – Knowledge Base
Welcome to the fourth and last module of this workshop. The purpose of
this module is to help all level of students, including people from the
beginner level, to build the knowledge base in order to achieve a set level
where they can gain further experience by means of setting up their own
virtual home lab.
This will be a short and quick module, as we need to present the setup of
the virtual lab as well as methods of hacking into databases by means of
tools, which doesn’t take much time, Ahan.
In the beginning of the workshop we focused on two database servers, if
you can recall, Microsoft SQL Server and MYSQL Server. However, so far
we were practicing on MS SQL Server. There is a big difference in these
two servers from their own architecture standpoint, however, SQL
Statements remains the same and there is not much difference. However,
the default views and features do differ to a large extent. We will cover
the hacking of MYSQL database by means of tools in this module so that
we cover both servers.
But the core of the SQLi attack is basically manual techniques and
customized queries which you have to write on your own in order to hack
into the backend database. Tools can perform all the work for you but
that’s not the way core hackers do it! Therefore, we will cover the usage
of tools to hack into the database servers in this module to cover both
methods of hacking databases.
Anyhow, so what do you need to develop your own virtual home lab?
The answer is simple; you need tools and virtual machine software, we
have explained that in other workshops as well, but as we mentioned, we
need to cover all types of students, it’s not necessary that all students
have gone through other workshops, too, or they already know how to
build home virtual lab. So students who have this knowledge, don’t worry,
sometimes it’s good to revise or you can jump this section easily.
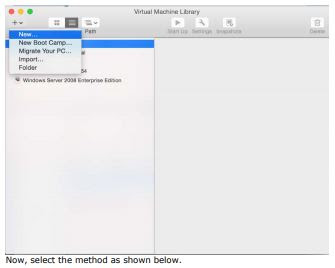
Setup Windows Server 2008
You can use virtual box as your virtual machine software, however, I am
running VMware Fusion on my Mac. Let’s setup VM for our server.
Setup MS SQL Server 2008
Now, you can either setup MS SQL Server 2008 Express edition or install
the full trial version for 180 days. It’s your choice, we have explained the
installation method for the 2005 express server in previous module,
however, installing the MS SQL Server 2008 would be bit different but you
can cover this easily as shown below.
Installing MS SQL Server requires PowerShell to be installed first, so let’s
do it quickly. For this open your server as shown below.
Download: http://www.microsoft.com/ennz/download/details.aspx?id=30438
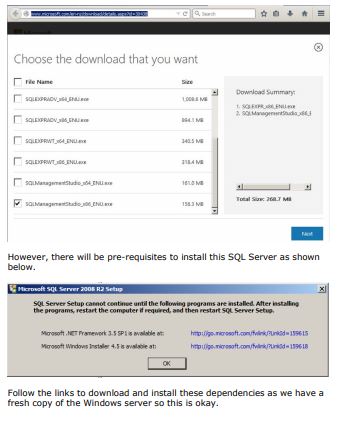
Download SQL Express and SQL Management Studio as shown in below
screenshot
Complete the installation as it’s simple to do so. After both installations
you will be required for reboot. Now, let’s move our focus back to SQL
Server installation.
Now, run the setup and you will see the following screen to start the new
installation
If all goes well then you will see the following screen confirming successful
installation.
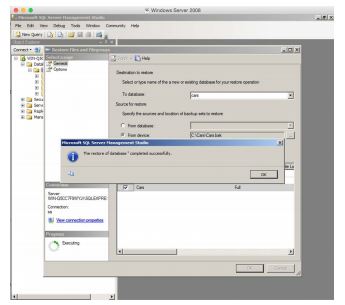
Now, install the management studio so that you can manage this server.
This should be okay as we did the SQL Server installation.
Tutorial 2 – Vulnerable Web Application Setup
Setup IIS Server on Windows Server 2008
Now, we will setup IIS Server, run the manager server and add the role
as shown below to install IIS Server.
Okay, now time to setup the database itself in the SQL Server we have
installed. For this we will provide the script to create database and sample
tables as well, however, you need to do it on your own as shown below.
Now run the management studio as shown below.
That’s it and now you have setup the database for the sample website we
will be running on the IIS Server we installed in the module.
Now, go back to the IIS Server and create the virtual directory and setup
the web application as explained below. You can run IIS Manager from
Administrative tools in control panel.
Once converted go to the following link on your browser for this web
application.
Link:
http://localhost/cars
You will be able to see the following web application up and running on
your Windows Server 2008 Server running IIS Web Server 7.
This web application is configured with the backend database we have
setup in this module. Now, it’s your time to add another web application
and start practicing the hacking as you learned in this workshop.
Hacking MYSQL & MS SQL Server with SQLMAP
As mentioned in the beginning of this module regarding the MYSQL
server, basically you don’t need to worry much about how it’s going to
work with tools. It’s easy indeed.
SQLMAP is basically written in python and it’s a free tool to execute
automated SQL Injection queries and unloads burden from your head and
save time in penetration testing.
We will give a vulnerable link, which has MySQL server running in
background so that we can demonstrate how quickly it works.
We have executed the target vulnerable URL, which we believe it’s
running backend database as MySQL and notice the same with SQLMAP.
Results are shown below.
You can notice that the backend database detected is MySQL server, and
you can play this server and dump all the content automatically with the
following switches:
--dump Dump DBMS database table entries
--dump-all Dump all DBMS databases tables entries
Moreover, you can take the shell on the victim machine too, however, and
can play with it in your virtual lab. Or if you want a more advanced
workshop which can lead to complete owning of underlying operating
system as well than do post on the forum so that we can bring that for
you separately in upcoming workshops, we can not execute this on live
web applications, however, we will develop the vulnerable lab
environment for dedicated labs with more advanced techniques.
We hope this workshop has been informative for you and we thank you for
completing this workshop.